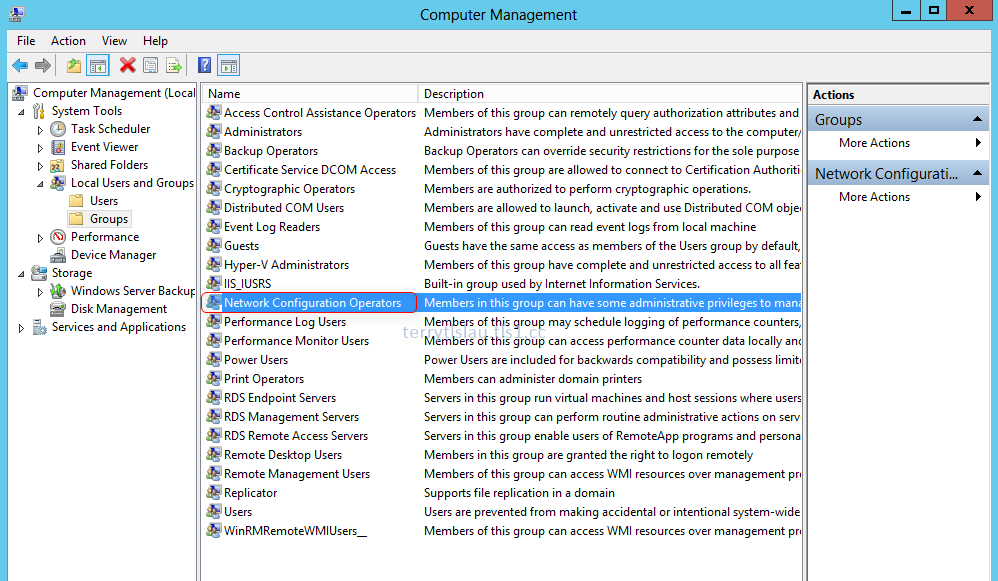
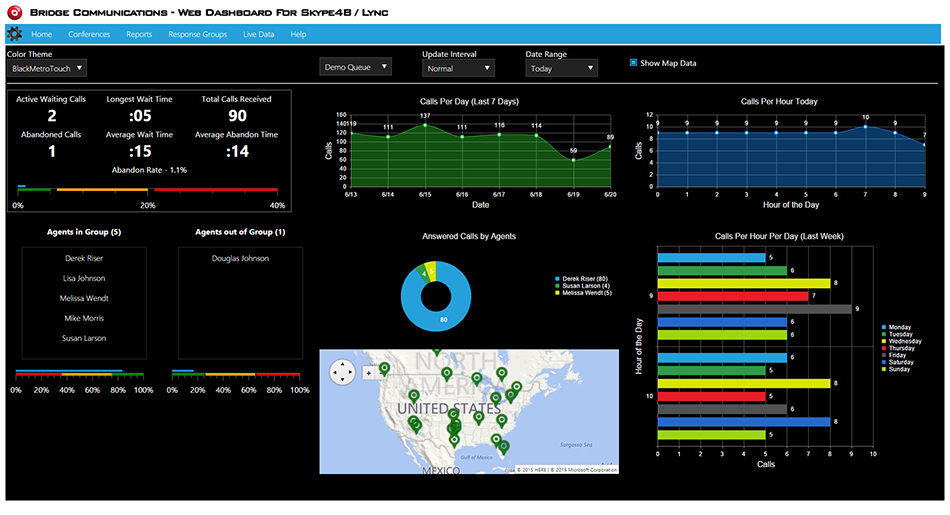
Stage 1: Reconnaissance. Russian state-sponsored cyber actors have conducted both broad-scale and targeted scanning of Internet address spaces. Such scanning allows these actors to identify enabled Internet-facing ports and services, conduct device fingerprinting, and discover vulnerable network infrastructure devices.
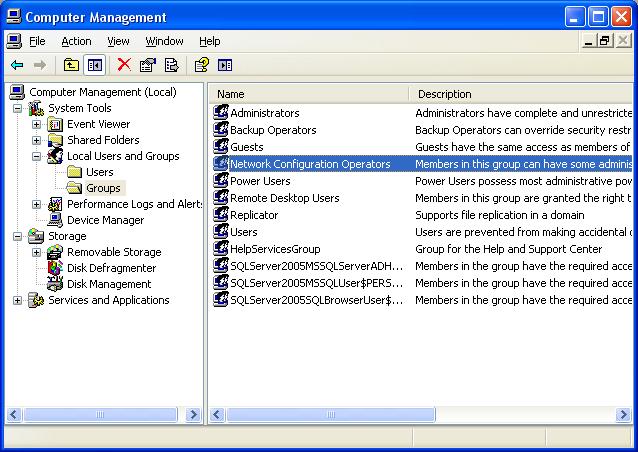
Prerequisites for Network Object NA T. Depending on the configuration, you can configure the mapped address inline if desired or you can create a separate network object or network object group for the mapped address (the object network or object-group network command).
The following page describes the configuration options available in MongoDB 3.6. For configuration file options for other versions of MongoDB, see the appropriate version of the MongoDB Manual. Using a configuration file makes managing mongod and mongos options easier, especially for large-scale
The Network Configuration Protocol (NETCONF) is a network management protocol developed and standardized by the IETF.It was developed in the NETCONF working group and published in December 2006 as RFC 4741 and later revised in June 2011 and published as RFC 6241.
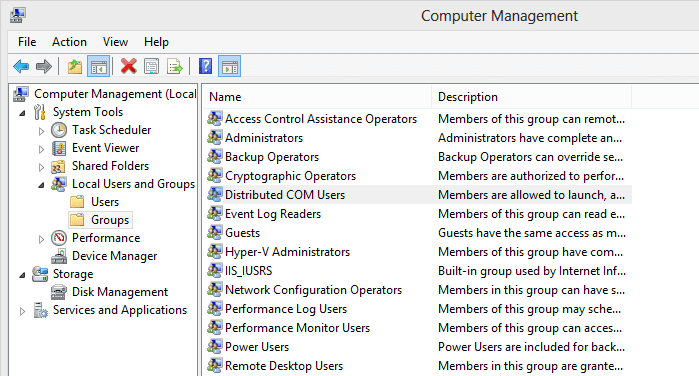

3. Network services. Network services enable a wide range of value-added functionalities for operators and users across all layers of the infrastructure.
LUSTER LightTech Group has been playing a leading role in the fields of Fiber Optics, Vision and Imaging since the establishment on June 6, 1996. With the goal of serving its customer with leading solutions, products and services, LUSTER organized products and solutions from more than 50 worldwide famous photonic and optoelectronic companies
Learn how to implement ISAKMP policies using IKE to ensure secure IPsec VPN configuration on a Cisco router.
K4USD Network. Supporting Amateur DMR Repeater Operators (Revised 04/12/2016) Amateur Radio Guide to Digital Mobile Radio (DMR): http://www.k4usd.org/guide.pdf The K4USD Network operates a c-Bridge cloud (currently 65 managers) and a development cBridge offering connectivity to the core DMR-MARC, NATS, DCI and Brandmeister …
The Dynamic Host Configuration Protocol (DHCP) is a network management protocol used on TCP/IP networks whereby a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on a network so they can communicate with other IP networks.
Supports IPv6. The ASA does not support IPv6 nested network object groups, so you cannot group an object with IPv6 entries under another IPv6 object group. You can mix IPv4 and IPv6 entries in a network object group; you cannot use a mixed object group for NAT. Additional Guidelines and Limitations